Configuring FOPE in Microsoft Office 365
Microsoft is eager to capture a greater share of the hosted messaging market through enhancements coming with Office 365 (the successor to its existing Business Productivity Online Suite, aka BPOS).
One add-on feature to sweeten the value is Forefront Online Protection for Exchange. FOPE, currently in version 11.1, provides antispam and antivirus protection for Office 365 mailboxes within your organization.
If you have never worked with FOPE before (and most people haven't), it can be a bit overwhelming initially. Here are five tips to make the process smoother:
1. Accessing FOPE Settings
You can spend hours clicking around the Office 365 Admin Console and never find the FOPE settings. There are actually two ways to get there: One is by logging into Outlook Web App (either directly or through the Admin Console) and accessing the Exchange Control Panel for your organization. (Select "Options, See All Options," then click the arrow next to "Manage Myself," choose "My Organization," and then select the "Mail Control" node.) You'll notice a link on the right side of the Mail Control options (shown in Figure 1) that you can click to access FOPE settings (shown in Figure 2). The second and quicker way is through Microsoft's FOPES site. You will need to enter your Office 365 user name and password to access the settings.
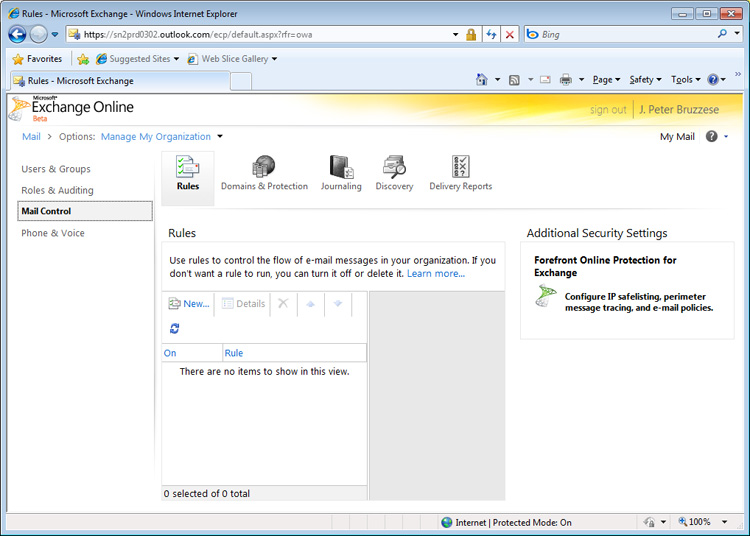
[Figure 1: FOPE Link From Your OWA Connection Through the Exchange Control Panel. Click to enlarge.]
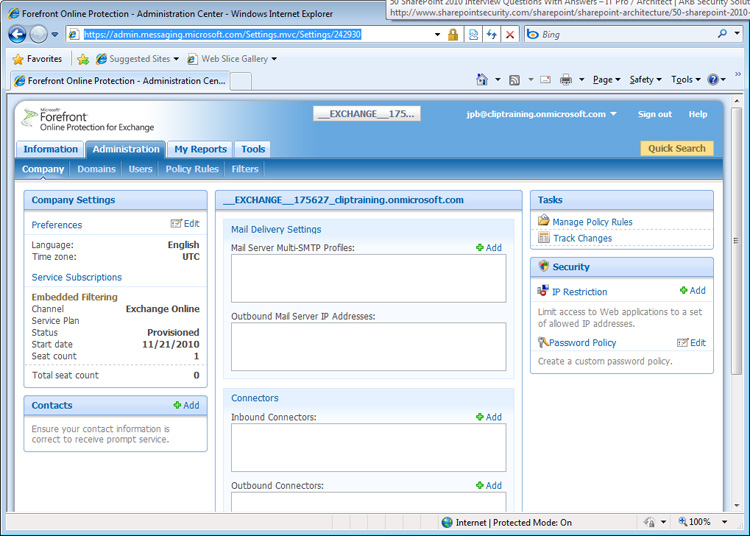
[Figure 2: What You See When You Log Into FOPE. Click to enlarge.]
2. At-a-Glance Information
The first tab you should select once you are looking at your FOPE portal is the "Information" tab (shown in Figure 3). From here you can see graphical visualizations of the organization and network filtering analytics. Announcements are also included on this tab, and you'll receive alerts about any service updates and enhancements.
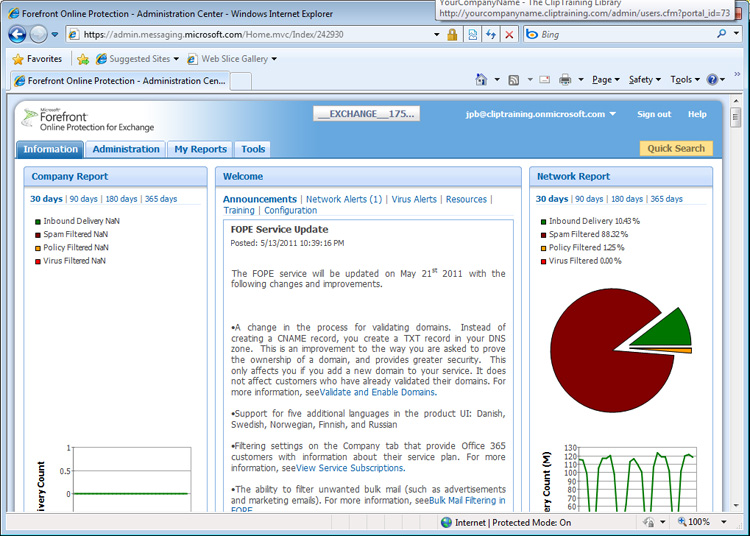
[Figure 3: The Information tab with at-a-glance visualizations]
3. Spam Action Settings
Antivirus protection scans are performed on all messages, both inbound and outbound, by Forefront Protection 2010 for Exchange Server (FPE) on the Exchange Online servers. No configuration is needed to perform any required action when a known virus comes in.
Spam is another story. You can configure spam settings, but only if you know where to look. To locate spam settings, select the "Administration" tab and then "Domains." You select the domain link for the domain for which you wish to edit spam policy. Scroll down to find the "Spam Action" options, and click the little "Edit" link to view your choices (shown in Figure 4).
There are four options:
- Spam Quarantine: The mostly widely used choice within large environments because it offloads the stress of processing and storing this junk mail. It is stored in a special web-based spam mailbox. Users can sort though these messages, which are purged after 15 days.
- X-Header: E-mail is delivered normally but a special X-spam header is inserted into each message's header to make offending messages easy to track as well as easier for system administrators to take action on the server and client sides. These headers mean sysadmins can configure transport rules (through Office 365's Exchange Control Panel) or client-side rules to handle problem mail.
- Spam Redirection: This option redirects e-mail to a specified SMTP within the domain for later review, typically by an syseadmin or someone appointed to check it regularly.
- Modify Subject: This will add a little identifier to the subject line (like the word SPAM) so users can easily identify spurious mail when they receive it.
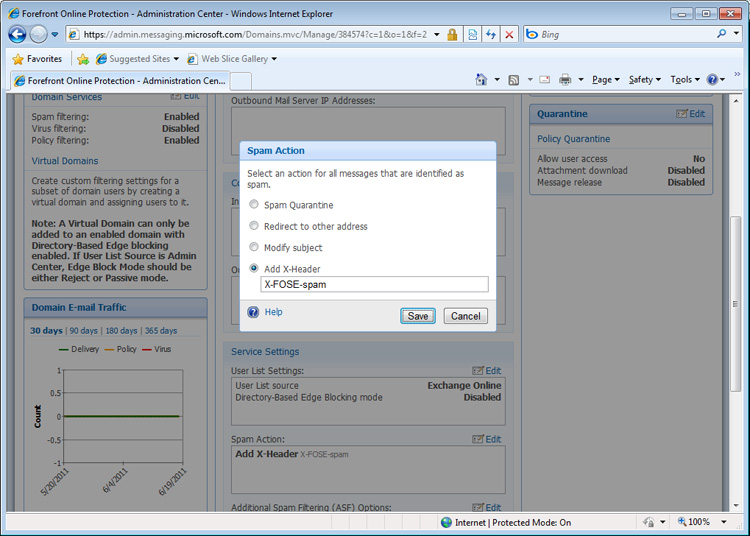
[Figure 4: Spam Action Settings]
4. Policy Rules
FOPE can do more than filter virus-laden and spammy messages. It let sysadmins enforce powerful policy rules, too. To locate these rules, select "Administration," click "Policy Rules," and then select the "New Policy Rule" link in the top right. The number of different settings is infinite. Learn more about FOPE policy enforcement on Microsoft's TechNet.
5. Additional Help
Currently, there's very little help-related information available about FOPE for Office 365 because the software launched in late June. You can find assistance on TechNet using the "Help" link in 365's upper right corner. But what's posted mostly focuses on standalone and Exchange Online users of FOPE, not users of Office 365. For the most part, the features available are the same - with a few exceptions.
To learn more about the new features that Microsoft has put into Office 365 that weren't available in BPOS, read our "Office 365 vs. BPOS" article.








