Watch Out for Breaking News – BizTech Quick Take
Searching for Breaking News More Risky than You Might Think
If a user goes looking for unsavory content at work — say, an adult website — most people would not be surprised if that user ended up being hit by malware. After all, naughty content attracts naughty behavior. But according to research by Websense, it’s actually riskier to cruise the web for breaking news and trends.
While doing research for our threat report we found that searching for breaking trends and current news represented a higher risk (22.4 percent) than searching for objectionable content (21.8 percent).
Most people get into trouble when they are busy doing something that isn’t useful—internet use included. OK, so what does this mean for you at work? Well, if you didn’t know it already, your new workforce is on the internet A LOT, and they expect to have internet access.
So, you’ve got workers wandering the net and at every moment they are just two clicks away from malware. Makes you stop and think a bit about the security defenses you have in place within your organization, doesn’t it?
So your users’ seemingly innocent lunchtime visits to celebrity gossip blogs and news sites could actually be more harmful to your network than you might think.
Read more about the dangers of web browsing on the Websense Insights blog.
8 Potential User Interfaces of the Future
Between The Jetsons, The Matrix and Tom Cruise’s Minority Report, showbiz has done a remarkable job of imagining the impossible when it comes to marrying humans and technology.
But sometimes the dream is beyond reach. For example, that flying car that George Jetson zips around in remains as elusive as ever to drivers in the real world.
However, the intelligent and inventive men and women at the MIT Media Lab are trying to make at least some of some of our futuristic tech dreams come true. The CIO Dashboard’s Chris Curran describes eight user interfaces of the future that these good folks are hard at work on right now. Here are a few:
Computerizing the World
With SixthSense, users wear a projector and camera around their neck in the form of a pendant that displays information about the world around them. Users can use hand gestures, arm movements or the object in sight to interact with the information being projected. The Fluid researchers contend that “SixthSense makes the entire world your computer.”
Merging Online and Brick-and-Mortar Shopping
The Augmented Product Counter uses augmented reality to transform any surface or object into an interactive surface. Soon customers will be able to research the reviews and pricing of products while they physically interact with the samples in the store. Merging online and brick-and-mortar shopping experiences has the potential to change shopping as we know it. CIOs in the retail sector should take note.
Writing in Space
Inktuitive is an “intuitive physical design workspace” that melds conventional design tools such as paper and pencil with the digital world. Imagine an architect sketching a blueprint of a building on paper while the design is instantly captured and translated into digital form.
Now, if only those kids at MIT can get to work on a real-life Mega Man power suit, we’d be all set for 2020.
Read more about the future of user interfaces in Curran’s post on the CIO Dashboard.
5 Questions to Test Your Company’s IT Security Plan
Think you’ve got your security issues all figured out? Are you confident that there’s no way malware proprietors can get their grubby hands on your company’s confidential data?
Then put your plan to the test with Matthew Rosenquist’s five-question cybersecurity test. Rosenquist, an information security strategist at Intel, believes that his quick test can precisely identify any weaknesses in any IT security plan.
Here are his five questions:
Question #1: Does your strategy identify the threat agents who will be attacking your organization over the next 3 to 5 years?
Without knowing the attackers, defenders remain in the dark and are forced to protect from threats both real and imagined. The first step to any realistic strategy is to know who the opposition is, both today and in the future. Thereby understand their capabilities, objectives, and likely methods.
Question #2: Does your strategy articulate how you will likely be attacked by those threat agents?
Understanding the computing ecosystem, where it is less secure, and how specific threat agents will attack over time is imperative to a strategy. Does the strategy talk about generic worms, viruses, and system patching, or does it take into account likely exploits paths. The ones which align to the common methods of those pervasive threat agents identified in Question #1?
Question #3: What impacts and losses are estimated from these attacks, given the expected defenses?
Strategy is about planning. Planning security is about finding the right balance between spending for controls and the losses prevented. Ultimately getting to a comfy place where the residual losses are acceptable for the cost of security. Without knowing the likely losses, even at a generic level, it is impossible to plan forward.
Question #4: How does your budget and efforts align to managing those losses? Does it fall within the range of acceptable levels of loss?
If you don’t have an accepted level of loss identified, you fail this question. Impervious security, where no losses occur, either do not exist or are far too costly to employ. Such a system is not practical. So, some losses must be accepted. Knowing this range is important to planning as it will trigger either growth or contraction for security spending
Question #5: Who is responsible for the care and maintenance of the security strategy?
Given the radical and chaotic nature of security threats, vulnerabilities, and impacts, a strategy must continually flex, adapt, and be updated. Without crisp ownership, most strategies rapidly become stale and worthless. Many such plans are rolled under some organization with little real stewardship. The manager of the group is therefore the 'owner', yet so far removed it is an invalid answer. If you don’t have the name of a single person, knows and agrees to actively manage the planning, you fail the question.
Read more about Rosenquist’s test on the Intel Open Port IT Community.
The ViewSonic ViewPad 10 Has One Foot in Windows 7 and the Other in Android
Who’s up for a 2-for-1 special? The fine folks at ViewSonic have uniquely decided to differentiate their tablet offering by bundling their tablet device, the ViewPad 10, with not one, but two operating systems.
The tablet ships with both Windows 7 Professional and the Android OS (2.2/Froyo), which allows for the standard productivity you’d expect from Windows-powered devices, combined with the mobility of the Android ecosystem.
Ramon Ray of smallbiztechnology.com caught up with Rommel Bugay, a senior product engineer for ViewSonic, who explained more about the device’s dual-OS appeal.
Watch the video below:
Read more about the ViewPad in the full post from smallbiztechnology.com.
Tenable Security Helps Sniff Out the Mobile Rats
Mobile computing is an incredibly liberating technology for the user, but for the network administrator, it’s become a source of concern.
This is particularly true of smartphones and tablets, which connect to both the enterprise Wi-Fi network and the broader 3G/4G networks of mobile carriers.
Tenable Security’s passive vulnerability scanner can help pinpoint which mobile devices are accessing your network, what information those devices are transmitting and what applications those devices are running. Which means you can harangue the marketing guy for monkeying around on Angry Birds for four hours of his workday. Information is power.
Here’s more from the Tenable Security blog on sniffing out mobile devices:
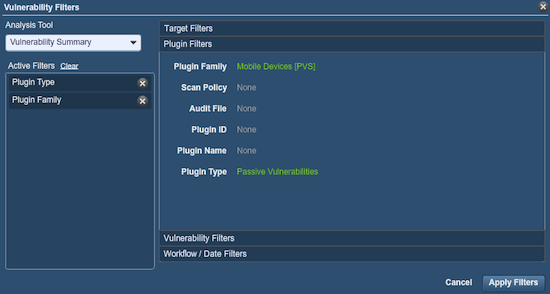
PVS plugins 4134, 5287, and 6067-6086 are dedicated to logging mobile devices and finding, where possible, the software/hardware version information of the devices. There is also a new plugin category called "Mobile Devices" in PVS that allows you to easily sort the data that has been collected. Devices that PVS can detect include tablets, mobile phones, e-book readers, and more.
Once you have found a mobile device, you can easily see what sort of traffic they have been passing or accessing on your network. For example, I've created the following filter in SecurityCenter:
The results of the filter showed the mobile devices in use at this facility:
Read more about mobile security on the Tenable Security blog.
Majority of USB Sticks Have Been Touched by Malware
As if you needed another reason to be wary of USB memory sticks, along comes the Naked Security blog with an interesting experiment that plainly shows the lax security of the average removable-storage user.
Paul Ducklin, head of technology for Sophos Security in the Asia Pacific region, recounts an intriguing experiment he and his team put together, in which they bought 57 lost-and-found USB sticks from the rail system in Sydney — and found that two-thirds of the sticks they examined were infected with malware.
Aside from the high prevalence of malware, there was also personal data uncovered on the USB sticks, which included:
- Lists of tax deductions
- Minutes of an activists' meeting
- School and University assignments
- AutoCAD drawings of work projects
- Photo albums of family and friends
- A CV and job application
- Software and web source code
Ducklin’s experiment proves that when it comes to removable storage, encryption is the key. It also shows that desktops and networks need to be protected from USB sticks because many of them are easily compromised without the average user’s knowledge.
Read more about USB sticks and IT security on the Naked Security blog.
Check This: The Small Business Remote Access Checklist
Work is a state of mind, not a place. While the office in most cases is the center of productivity, in the event of a disaster, it’s critical that work be able to continue elsewhere.
Of course, there are other reasons for using a remote-access solution; among them, convenience and flexibility for workers who do the bulk of their work in the field.
Read the BizTech Small Business Remote Access Checklist to make sure you’ve crossed your t’s and dotted your i’s when it comes to the mobile workforce.
Find more great content from the bloggers listed here and other IT blogs by checking out our 50 Must-Read IT Blogs.